OT SECURITY
BUILT-IN PROTECTION
AGAINST OT THREATS
—BEFORE THEY CAUSE HARM.
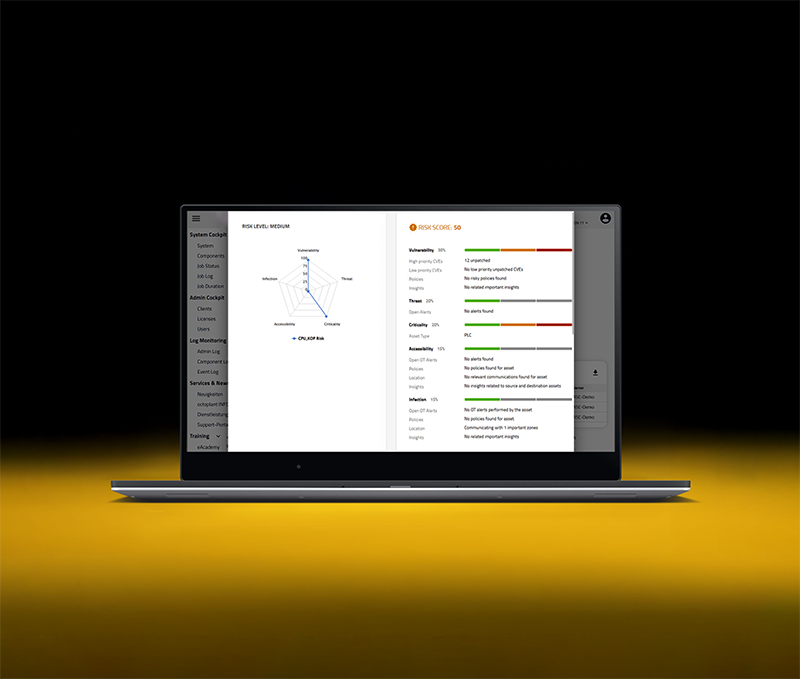
Octoplant strengthens cybersecurity in industrial control environments by delivering full visibility into known vulnerabilities and tracking every change made to critical systems. Instead of relying on active scanning, octoplant matches asset data with CVE databases and prioritizes risks using criticality scores, helping teams act fast where it matters most.
Built for operational technology, it supports NIS2 and NIST compliance by offering transparent asset documentation, version control, and recovery. As more systems become connected, octoplant ensures that threats like unauthorized access, misconfigurations, or outdated firmware are detected early – enabling both prevention and fast response.
Enhanced Security Profile
Map known CVEs to devices across your network to understand where your vulnerabilities lie – without active scanning or interference.
Change Detection
Track unauthorized edits and configuration changes with notifications. Every discrepancy is automatically captured in backup versions.
CVE Mapping and Assessment
Automatically match device data with CVE databases and assess risk using CVSS scores. Prioritize high-risk vulnerabilities with clarity.
Compliance Management
Meet NIS2 and NIST requirements through structured asset visibility, change tracking, and incident recovery capabilities.
Multi-Site Scalability
Deploy OT vulnerability management across all locations – with unified insights, consistent processes, and centralized reporting.
Automated Threat
Intelligence
Intelligence
Benefit from continuous CVE updates and adaptive detection without manual scans. octoplant evolves as threats change, keeping your defenses current.
Secure the Core of Your Operations
Cyber threats targeting operational technology often begin where devices are configured and changes occur. octoplant embeds security at the core of the automation layer, monitoring configuration changes, mapping known vulnerabilities, and providing asset-specific risk insights.
By focusing on the automation where threats can originate — not just the network perimeter — octoplant empowers manufacturers to detect, prioritize, and respond to risks before they impact production. This internal visibility strengthens every layer of the environment, helping teams build resilient, secure operations from the inside out. It also reduces reliance on intrusive scanning tools, making it ideal for sensitive, legacy-rich environments. With octoplant, security becomes a continuous, automated part of daily operations — not just an emergency response.

